
サイクリングも模型作りも時間ないので
Posted on Thu 28 April 2022 in development

Posted on Thu 28 April 2022 in development
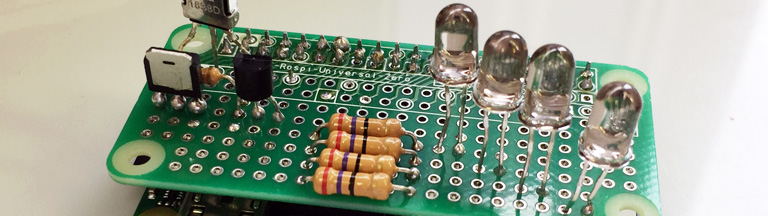
Posted on Wed 29 July 2020 in development • Tagged with iot, raspberry pi

Posted on Thu 18 June 2020 in development • Tagged with debian
Debian GNU/Linux 10 Buster上でアースソフトのPT2を利用してテレビ番組録画環境を構築しました。MirakurunとEPGStationを使いこなせているかまでは不明です。

Posted on Fri 25 October 2019 in plasticmodel • Tagged with mobile suit, gunpla, nograde, gelgoog

Posted on Fri 06 September 2019 in plasticmodel • Tagged with mobile suit, gunpla, nograde, gelgoog

Posted on Sat 02 February 2019 in plasticmodel • Tagged with mobile suit, gunpla, nograde, gouf
気まぐれに1/100グフを取り出して組み立ててみることにする。1/100グフは4つ持っているというのに、これまで一度も作ったことのないキット。どんなきっと何だろうということでささっと仮組みしてみることにする。

Posted on Thu 20 December 2018 in plasticmodel • Tagged with mobile suit, gunpla, nograde, gundam

Posted on Mon 12 November 2018 in plasticmodel • Tagged with mobile suit, gunpla, nograde, gundam
当時作った1/100ガンダムを再び。今では旧キットと呼ばれるようになったRX-78ガンダム。このロケットランチャーは何?というあきらかにおもちゃ路線のキット。ここからガンプラが流行るのかと思うと懐かしいというか感慨深いものです。

Posted on Fri 08 December 2017 in plasticmodel • Tagged with mobile suit, gunpla, nograde, z'gok

Posted on Tue 30 May 2017 in plasticmodel • Tagged with mobile suit, gunpla, nograde, zaku ii
旧キット1/144の量産型ザクです。少し前に無改造で製作してます2つ目です。今回は、ガンプラ好きな中学生に同じ量産型ザクをプレゼントして、作ってみよう!ってことではじめました。そのまんまはすでにやっているので、小改造でそれっぽくというのを目指してみました。